Using a Switch as Port Extender for Threat Defender (Breakout Mode)
Using a VLAN-capable switch as port extender, you can connect Threat Defender to your LAN and intercept the network traffic, i.e. apply policies to the traffic.
Tip
This approach differs from setting up a mirror port where Threat Defender only sees copies of the packets but cannot intercept them.
On the Switch
Assign VLAN tags 301-348 to each port of the switch. We recommend mapping VLAN tag 301 to port 1 and so on. Refer to the documentation of your switch for further information.
Set up one port as trunk port that contains all tagged VLANs.
Connect the trunk port of the switch to Threat Defender. In this example, we connect the trunk port to interface
enp4s0.
Note
With this setup, the switch cannot transmit any other VLAN-tagged traffic.
On cognitix Threat Defender
Navigate to Network > Manage Processing Interfaces.
Click Add to create a new bridge.
Enter a Name for the bridge.
Under Port, select the interface connected to the trunk port of the switch, i.e.
enp4s0.Enter the used VLAN Range, i.e.
301-348.Save the bridge.
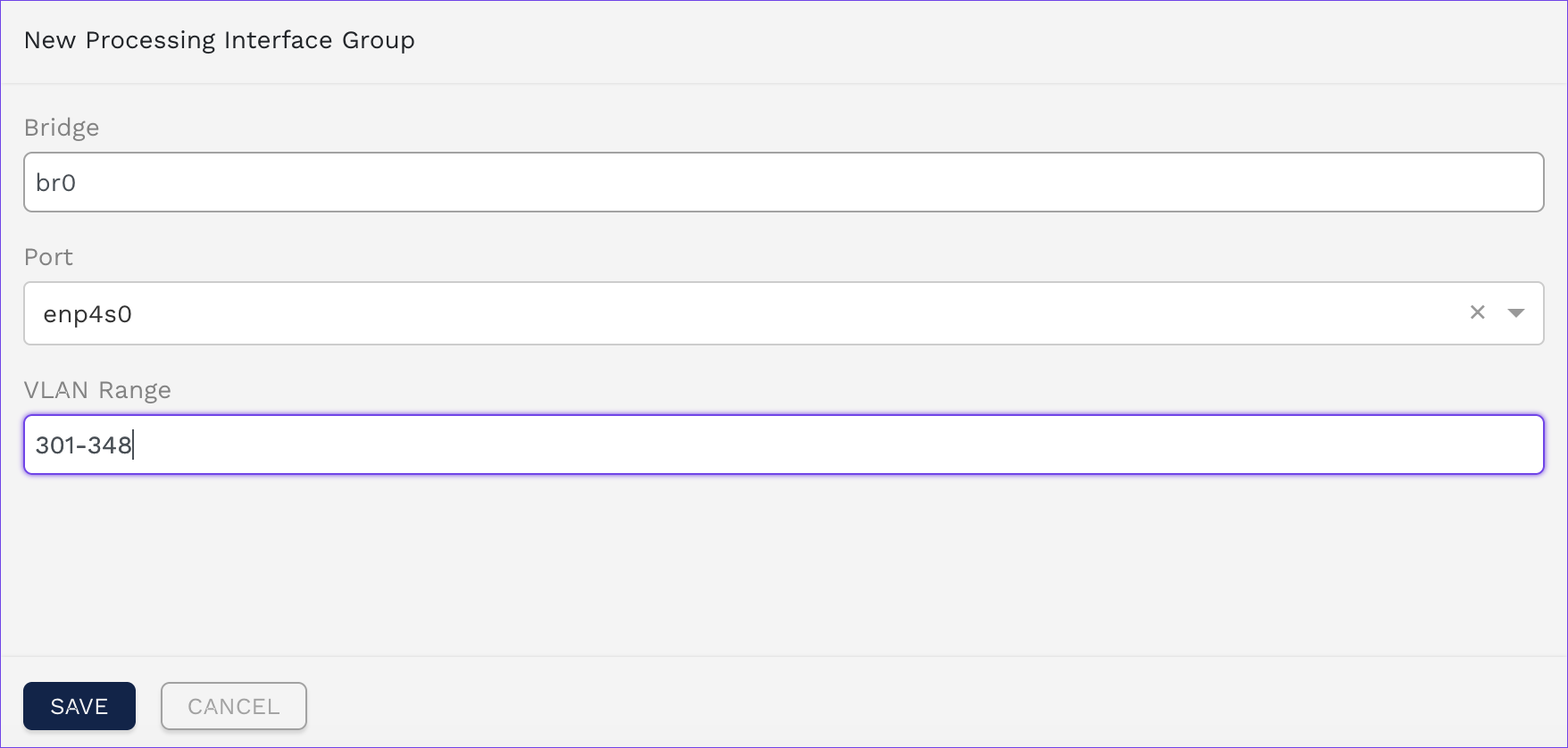
Example interface setup.
Disable the default interface configuration, i.e. set the slider switch to
 .
.Click the APPLY CHANGES button in the header to activate your configuration changes.
Result
All the physical ports of the switch are now bridged via their VLANs on the selected interface. Threat Defender can now intercept the communication going through the switch via the assigned VLAN tags.

The switch handles VLAN traffic.