Network Integration
When using Threat Defender in your switched network, keep in mind that only traffic that passes Threat Defender can be analyzed.
Threat Defender operates on layer 2 of the OSI model, i.e. the data link layer. It is transparent to the network so that it can be integrated into the network at any point - not just between network segments.
Due to its network switch characteristics only the sending and receiving ports can see the traffic. For this reason, place Threat Defender in front of the switch to protect the network behind it.
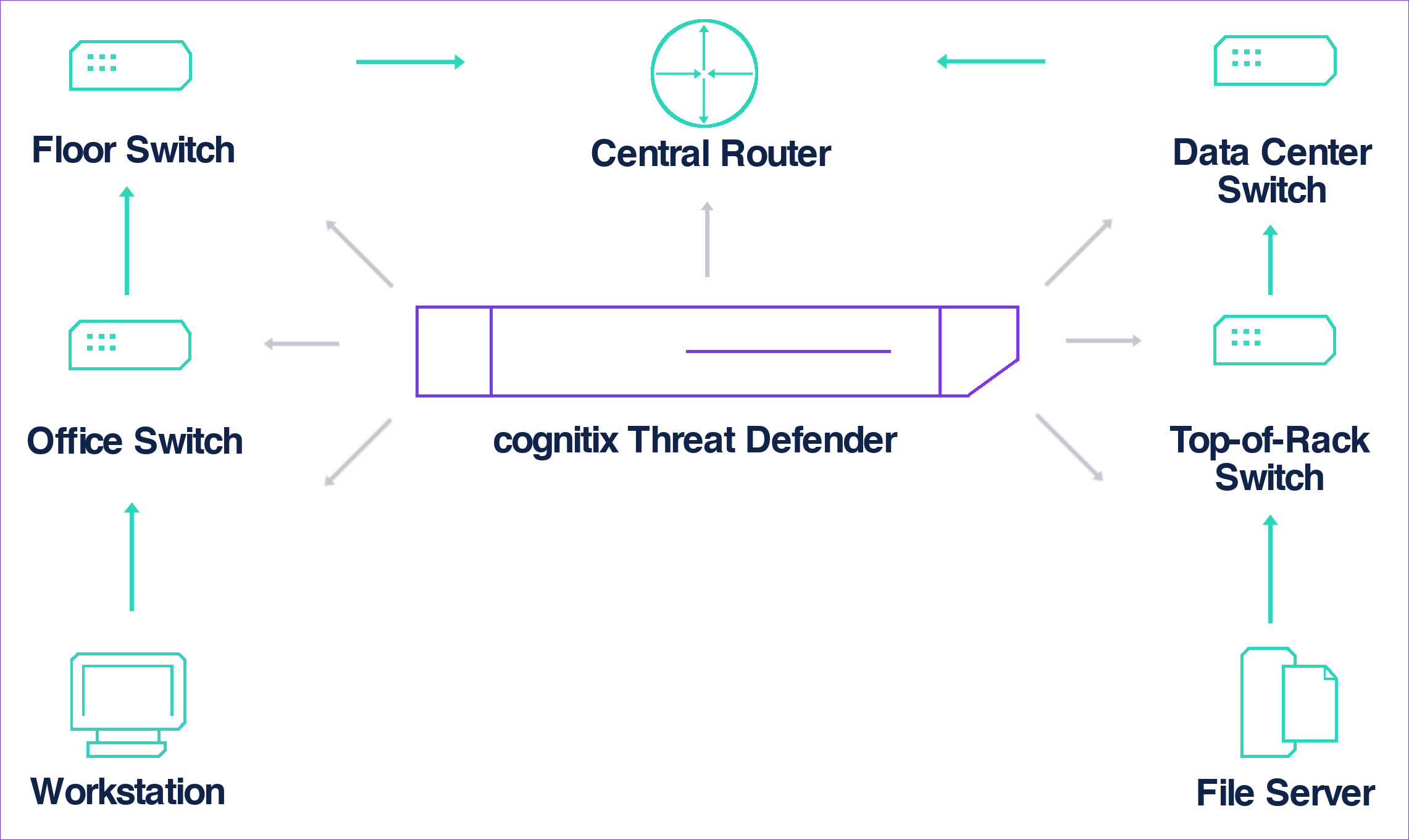
Connections where Threat Defender can be deployed to increase network visibility and security.
Depending on its intended use, there are different ways of deploying Threat Defender:
If you just want to monitor the network traffic for the devices connected to a switch, you can configure the switch to send all packets as a copy to the device Threat Defender is connected to (mirroring or switch monitoring). For further information, see the documentation of your switch.
If you want to secure parts of your network, make sure that all packets pass Threat Defender. You can use a separate switch for the critical network part and connect Threat Defender between.
Tip
Integrating Threat Defender actively into the network does not impact performance because the policy is always evaluated. This means even when Threat Defender is used for port mirroring, the policy is evaluated for analytics purposes.