Port Monitoring
Using policy rules cognitix Threat Defender can monitor individual ports and generate log entries when it sees unexpected traffic.
In the following example, Threat Defender monitors port 443, the default port for HTTPS traffic. If other traffic, such as SSH or VPN, is rerouted to port 443 this may indicate attempts to circumvent network restrictions.
cognitix Threat Defender logs warnings for any traffic other than HTTPS on port 443.
Create the Rule
Create the following global rule:
Source Networks |
Destination Networks |
Conditions |
Actions |
|---|---|---|---|
|
|
Layer 4 Port |
Log: |
For detailed instructions on how to create a rule, refer to Create Global Rules.
With the above rule, Threat Defender will generate incident log entries for all traffic via port 443, other than HTTPS. But it will not intercept the traffic.
Tip
You can expand this rule as required. For example, if you want to avoid creating incident log entries for certain protocols or traffic from specific sources, you can exclude them as well.
Result
You can see the rule hits in the reporting.
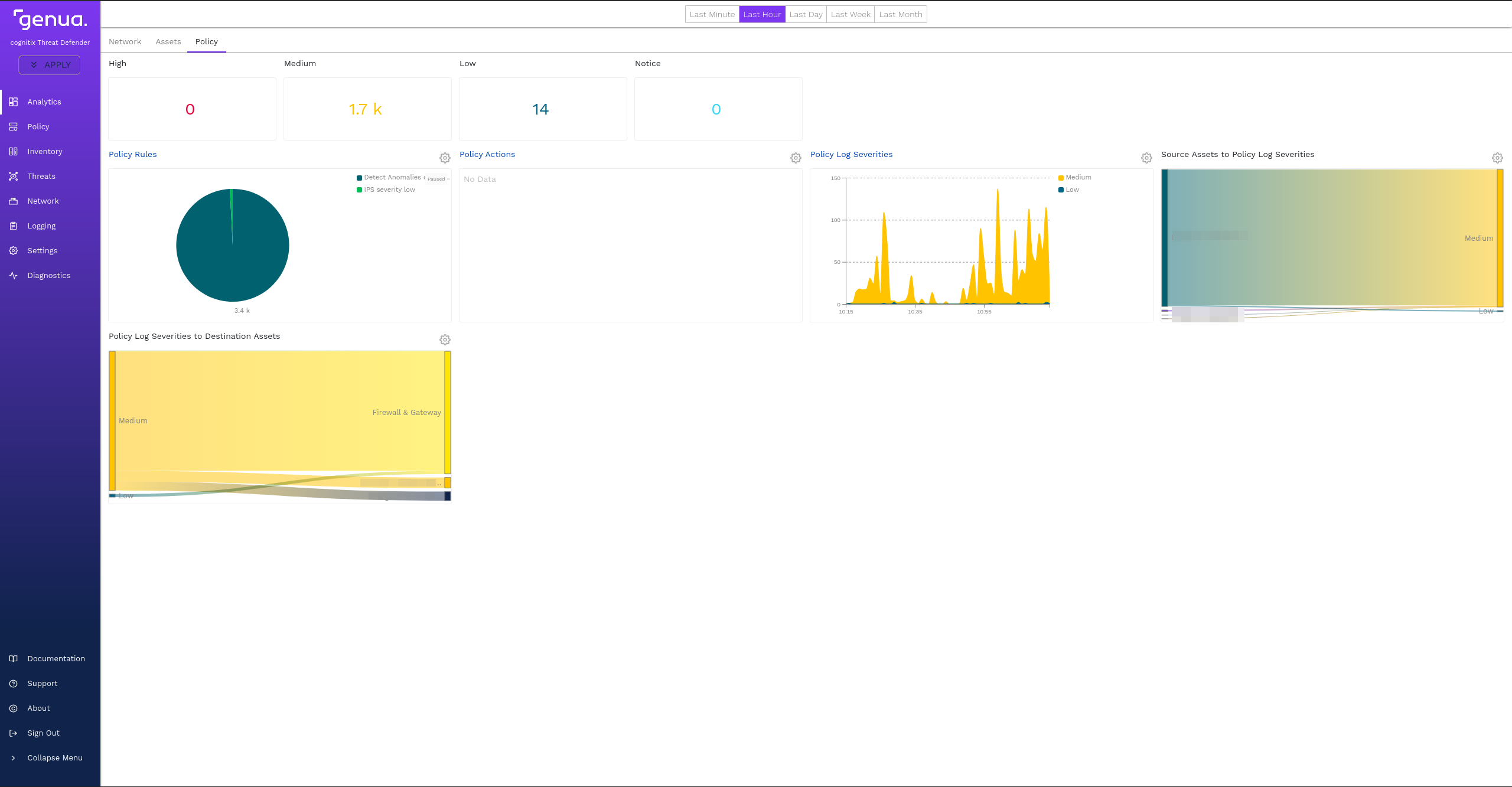
The rule hits seen under Analytics > Policy.
The incidents logs show warnings with severity Medium for all traffic on port 443 that is not HTTPS.
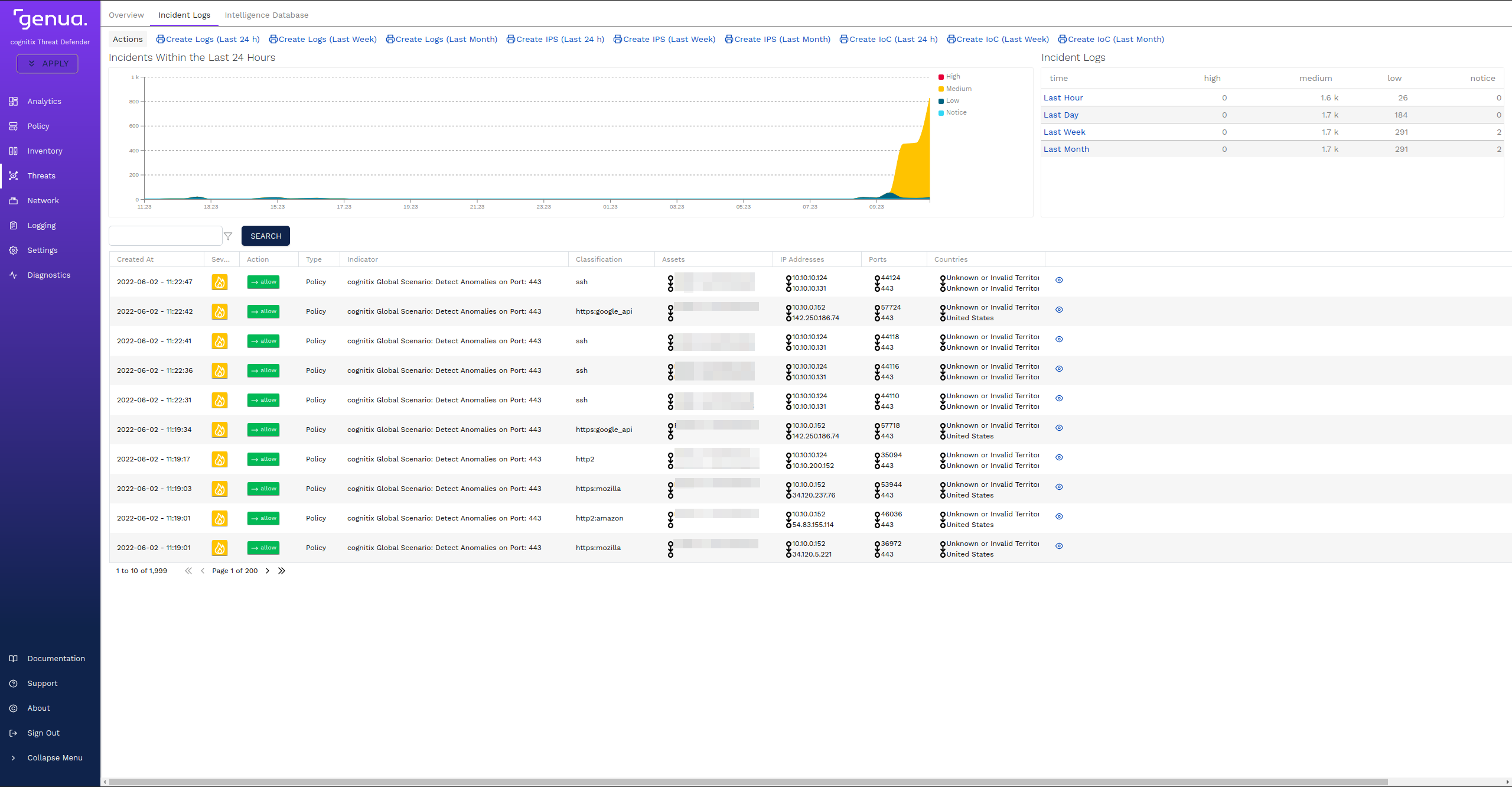
The incidents log entries under Threats > Incident Logs created by the rule.
Starting at these screens, you can further analyze the anomalous traffic via port 443. If cognitix Threat Defender is active in the network, you can then create additional rules to actively block unwanted traffic.
Additional References:
For information on the incidents logs, see Incident Logs.