Passive Monitoring
cognitix Threat Defender monitors the network to increase trancparency. Using rules, it tracks assets, communication flows, and so on. These rules can generate log messages if unexpected or anomalous behavior is detected.
This provides clear visibility of the network traffic and active assets. Using the intuitive drill-down reporting system of Threat Defender you can analyze this information.
To passively monitor the network traffic without intercepting it, connect cognitix Threat Defender to the mirror port of a switch (mirroring or switch monitoring). You need to configure the switch to send copies of all packets to the mirror port. For further information, see the documentation of your switch.
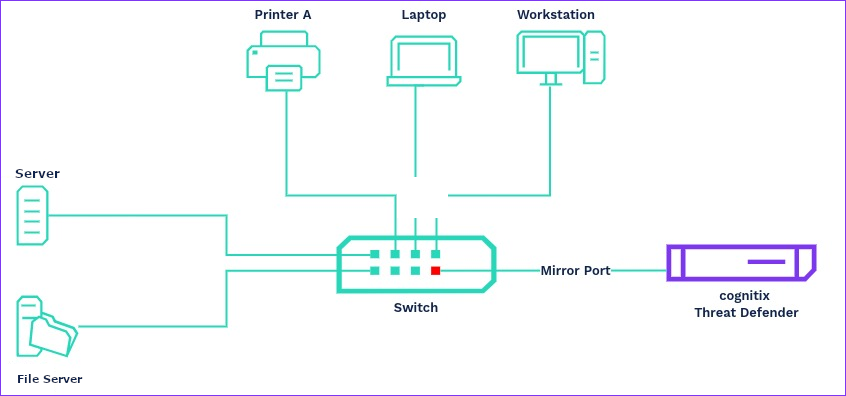
cognitix Threat Defender connected to the mirror port of the network switch.
In this mode, cognitix Threat Defender aggregates reporting data and logs on the network traffic seen at the mirror port. The traffic is not intercepted and VLAN tags remain untouched.
The reporting system of Threat Defender allows you to analyze the traffic. Drill down from the high-level dashboards to detailed analysis screens.
The following chapters provide a starting point for your network analysis: