Define the Policy
The policy in cognitix Threat Defender consists of global rules and correlation scenarios.
Navigate to Policy > Rules to see the current policy. Global rules are placed at the top of the policy table. Rules used in correlation scenarios are grouped by scenario.
These rules and scenarios are processed from top to bottom.
cognitix Threat Defender checks for each rule if the current traffic flow meets its conditions. If yes, it carries out the specified rule actions. If not, it checks the traffic against the next rule.
Note
cognitix Threat Defender has a blacklisting approach to rule processing. This means if the policy contains no rules or if a specific traffic flow matches no rules, its traffic is allowed by default.
Flows are evaluated against the policy for each new packet that updates the flow. This means a traffic flow practically continues to cycle through the policy until it ceases.
The following image illustrates the policy processing of Threat Defender.
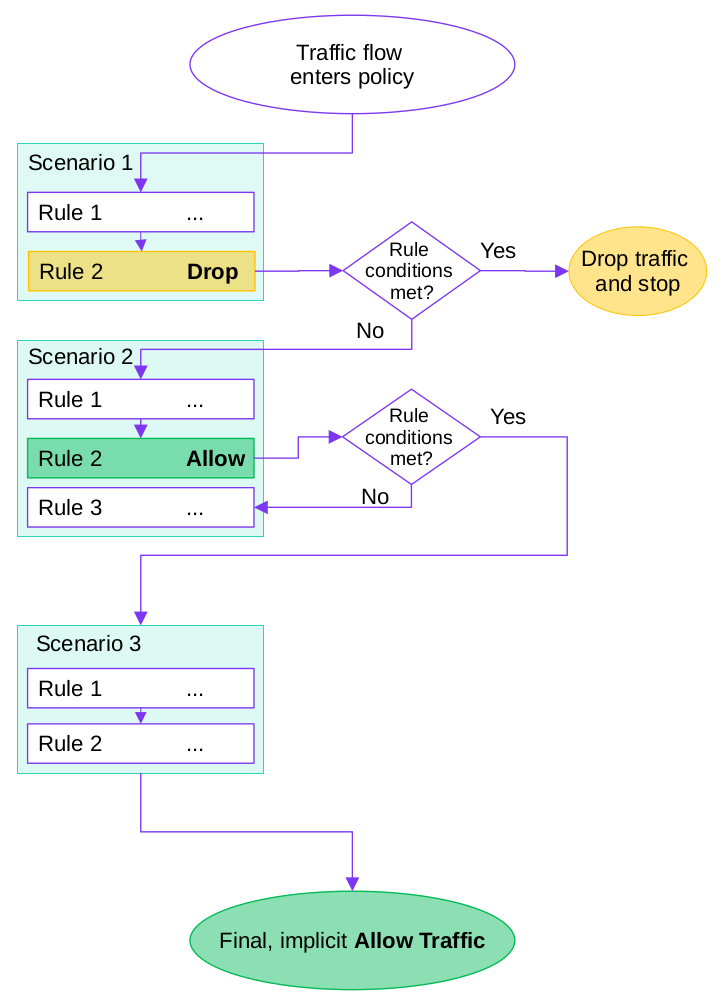
Example processing sequence.
Rule actions are performed on the traffic flow, if a rule matches. When no action is selected, Threat Defender will evaluate the traffic flow against the next rule in the policy.
Final actions define how Threat Defender will continue to process the traffic flow. There are the following final rule actions:
Allow Traffic and Skip to Next Scenario
Traffic matching this rule is not intercepted. This means that cognitix Threat Defender exits the current scenario for this traffic flow and continues to correlate it with the next scenario in the policy.
Drop Traffic and Stop Processing
Traffic matching this rule is silently dropped, i.e. the packets are silently discarded. Rule processing for this traffic flow ceases.
Reject Traffic and Stop Processing
Traffic matching this rule is actively rejected, i.e. all parties are notified by TCP reset (if possible) that the packets are discarded. Rule processing for this traffic flow ceases.
Additional References:
For information on behavior-based correlation in general, see Correlation in Threat Defender.
If you want to look up the settings options for rules and correlation scenarios, refer to Policy in the interface reference.