About this Manual
This manual describes cognitix Threat Defender (or Threat Defender for short) build 20221013.1.0. For an overview of the most significant changes in this build, see What’s new in this version?
To search for content in the manual, you can use the search field at the top of the navigation. To be able to use the search, you need to have JavaScript enabled in your browser.
You can switch between the English and German manual by clicking the respective link at the top of each page.
This manual is available in HTML and PDF format. You can open the PDF version by clicking at the link at the top of each page. The PDF will be in the same language as the HTML version.
Intended Audience
This manual is for network administrators and technicians who are responsible for installing and configuring cognitix Threat Defender as well as defining the network policy.
To be able to use this manual effectively, a solid background knowledge and experience regarding networking concepts is required.
Conventions
The following typographic conventions and notations are used to represent information in this manual.
Elements of the graphical user interface are indicated as follows:
Buttons, checkboxes, list names and other GUI items appear in bold font.
List options and literal text appear in a
fixed-width font.A sequence of menu commands is indicated as follows: Policy > Network Objects > Static Network Objects. In this case, go to the Policy menu, select Network Objects and open the Static Network Objects submenu.
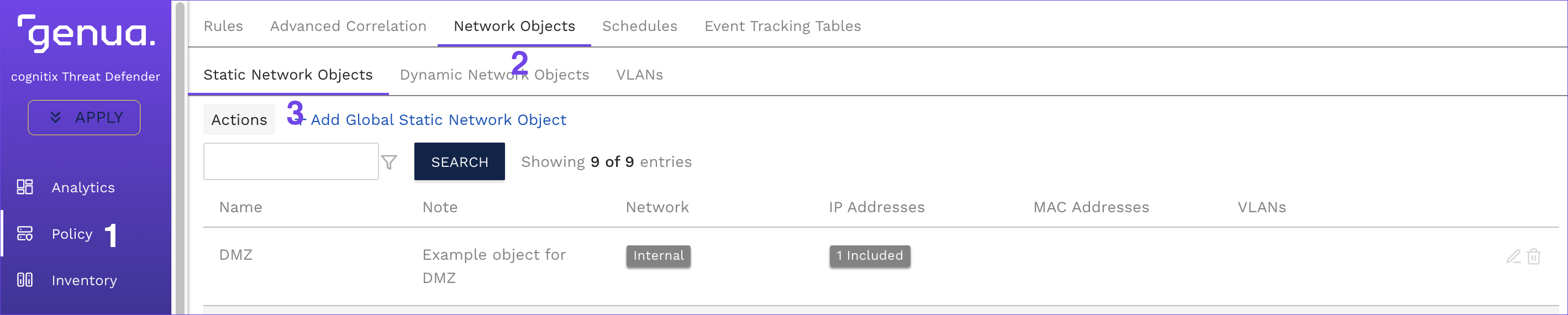
Policy > Network Objects > Static Network Objects
Links appear as violet text.
Glossary terms appear as green text. Click the term to jump to the respective section in the glossary.
The following types of notes are used to indicate additional information or call attention to a particular point:
Tip
This note contains useful tips that make your work easier.
Note
This note contains important information.
Warning
This note contains information that is very important to consider. If it is not observed, network security may be at risk.