Active Network Integration
When cognitix Threat Defender is active in the network, it can intercept the network traffic. This allows it to detect complex attacks and to initiate countermeasures.
When using cognitix Threat Defender in your switched network, keep in mind that only traffic that passes Threat Defender can be analyzed.
Threat Defender operates on layer 2 of the OSI model, i.e. the data link layer. It is transparent to the network so that it can be integrated into the network at any point - not just between network segments.
Due to its network switch characteristics only the sending and receiving ports can see the traffic. For this reason, place Threat Defender in front of the switch to protect the network behind it.
If you want to secure parts of your network, make sure that all packets pass Threat Defender. You can use a separate switch for the critical network part and connect Threat Defender between.
Tip
Integrating Threat Defender actively into the network does not impact performance because the policy is always evaluated. This means even when Threat Defender is used for port mirroring, the policy is evaluated for analytics purposes.
The following examples illustrate how cognitix Threat Defender can be used inside the network.
Example 1: cognitix Threat Defender in Breakout Mode
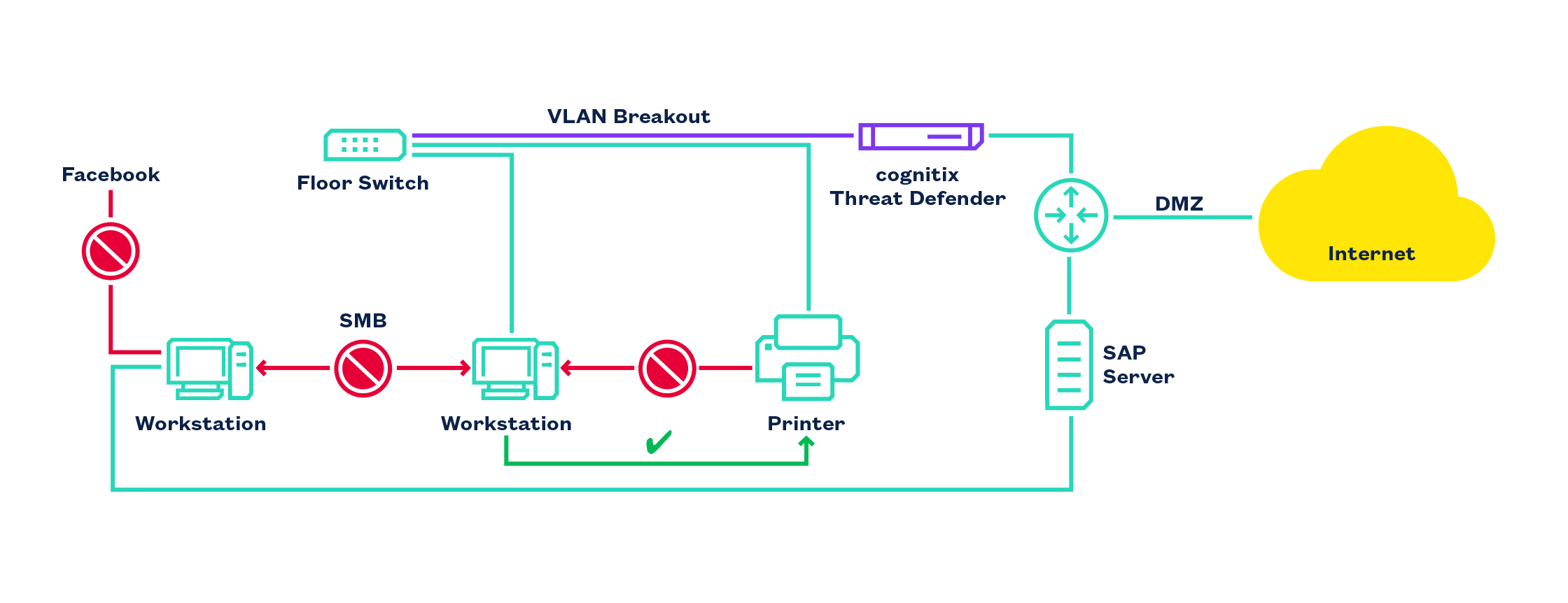
cognitix Threat Defender in VLAN breakout mode.
In this setup, Threat Defender acts as a switch with security functionality. It monitors the traffic and enforces the security policy:
Clients may access the SAP server.
Clients accessing the SAP server must not access Facebook at the same time.
Clients must not share files among each other to stop lateral movement of attackers.
Clients may access the printer but the printer must not access clients.
See also Use a Switch as Port Extender for Threat Defender (Breakout Mode).
Example 2: cognitix Threat Defender in a DMZ
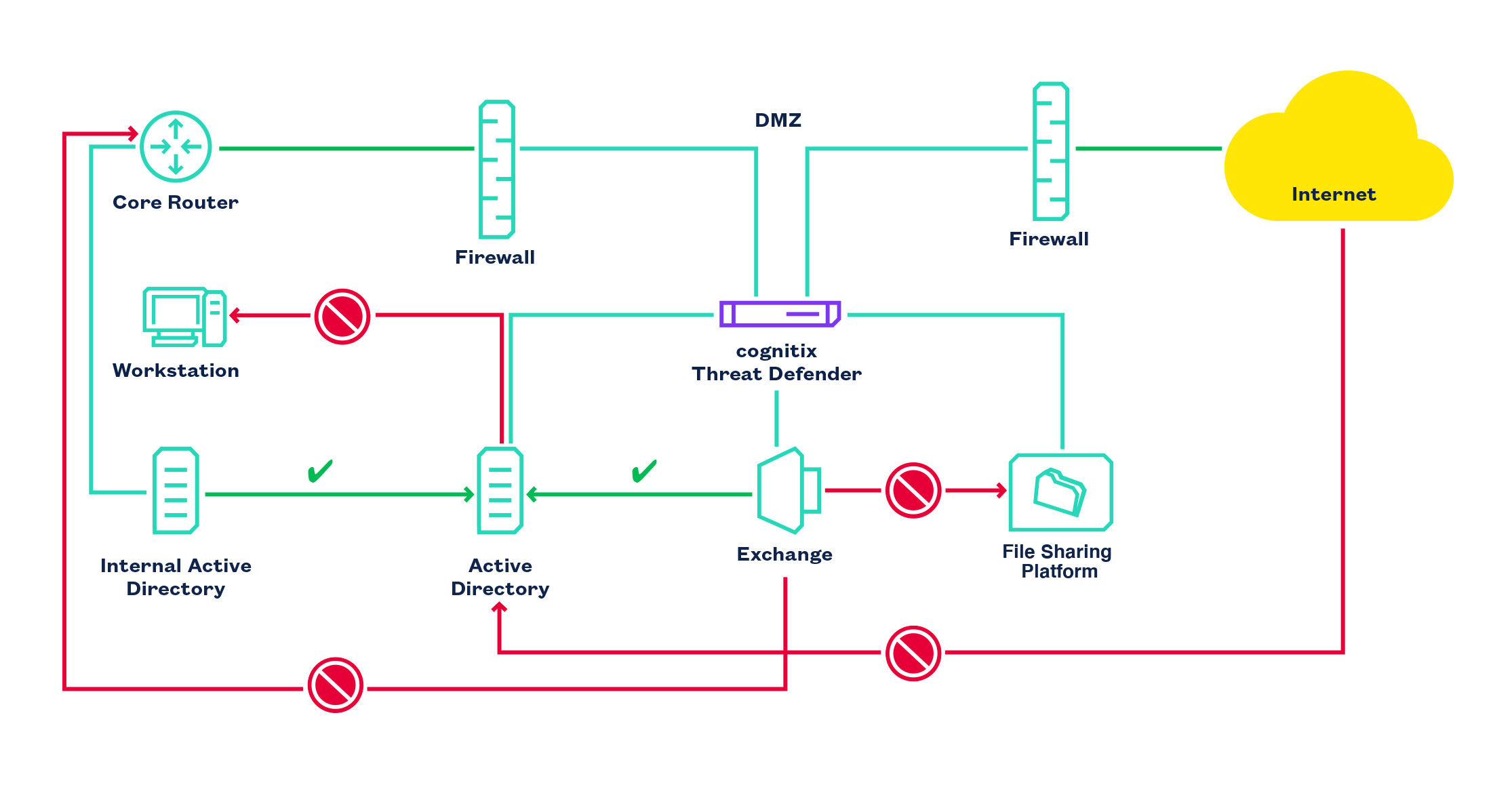
cognitix Threat Defender isolates services in a DMZ.
This DMZ setup adds additional prevention of DoS attacks on public services. It also prevents lateral movement of attackers within the DMZ and into internal networks. cognitix Threat Defender isolates the services inside the DMZ from each other and allows only the necessary communication:
Exchange may communicate with Active Directory.
But Exchange must not communicate with the file sharing platform.
Exchange must not access the internal network.
Active Directory must not contact any clients.
An internal Active Directory is allowed to access Active Directory in the DMZ.