Adaptive Behavior-based Graylisting
Objective
Threat Defender can be set up to continuously learn (and forget) normal behavior to create an adaptive baseline. When suspicious behavior is detected, traffic from the respective client is graylisted. It is then compared to the learned behavior so that unknown behavior is blocked and only the learned normal behavior is allowed. This way the system stays operational while threats are stopped and cannot spread.
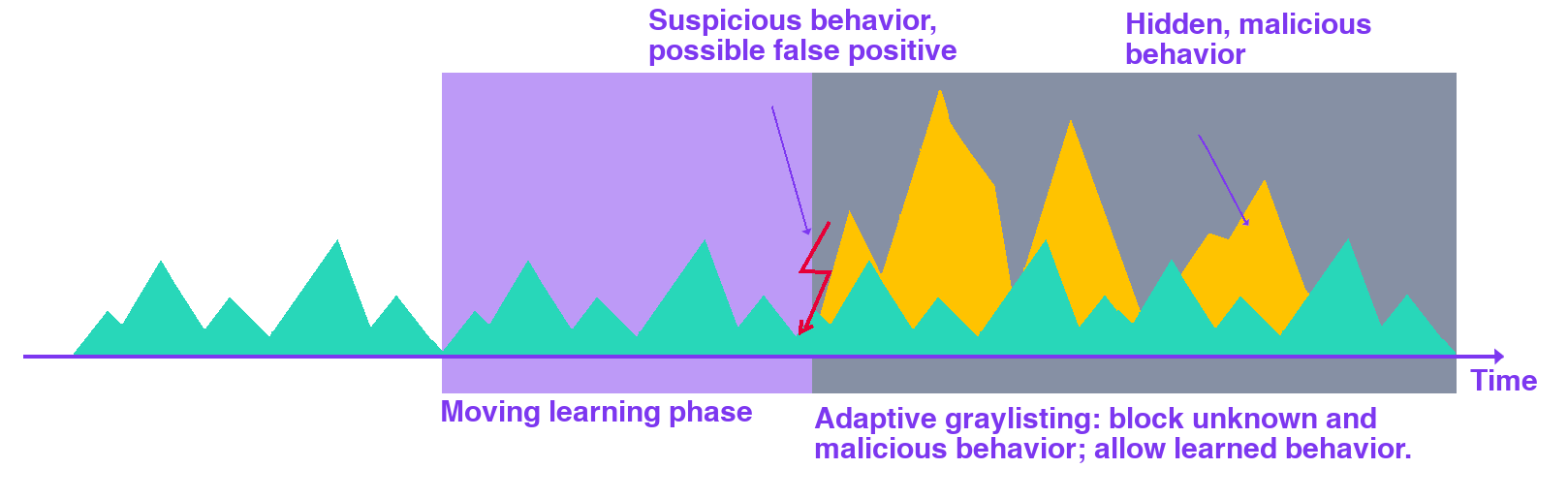
Adaptive behavior-based graylisting.
A dynamic network object stores the MAC addresses of suspicious clients for an hour. An event tracking table stores the learned communication paths for 24 hours, creating a moving time window for baseline learning.
Creating the Correlation Scenario
First, navigate to Policy > Advanced Correlation. Create a new correlation scenario that provides the framework for the required dynamic network object, event tracking table and rule set.
Creating the Dynamic Network Object
In the correlation scenario, open the Dynamic Network Objects tab. Create a dynamic network object that stores the client MAC addresses of suspicious clients for one hour.
The following table shows the required settings of the dynamic network object:
Name |
Network |
Size |
Timeout |
|---|---|---|---|
|
Internal |
|
|
For detailed instructions on how to create a dynamic network object in a correlation scenario, refer to Creating a Dynamic Network Object.
Creating the Event Tracking Table
In the correlation scenario, create an event tracking table. It stores the source (client) MAC addresses per destination (server) IP address.
The following table shows the required settings of the event tracking table:
Name |
Retention Time |
Primary |
Max. No. Primary |
Secondary |
Max. No. Secondary |
|---|---|---|---|---|---|
|
|
|
|
|
|
Note
Under Maximum Number of Primary Attributes, make sure that the table is large enough to fit your network traffic.
For detailed instructions on how to create an event tracking table, refer to Creating an Event Tracking Table.
Creating the Rule Set
The following rules are needed for Threat Defender to learn traffic patterns and reject suspicious or unknown traffic.
Rule 1 adds clients that trigger a threat intelligence hit to the dynamic network object
Suspicious Clients.Rule 2 checks the communication destinations of clients in
Suspicious Clients. If the communication destination is stored in the event tracking tableLearned Communication, the traffic is allowed. Otherwise, Threat Defender continues processing the next rule.Rule 3 drops traffic from clients in
Suspicious Clients, because this is unknown traffic.Rule 4 tracks the source and destination for all clients that are not in
Suspicious Clientsin the event tracking tableLearned Communication. This allows Threat Defender to learn normal communication.
Rule |
Source |
Destination |
Condition |
Actions |
|---|---|---|---|---|
|
|
Threats Indicators |
Dynamic Network Object: |
|
|
|
Advanced Correlation Conditions: |
Final Action: |
|
|
|
Final Action: |
||
|
|
Add to Event Tracking Table |
For detailed instructions on how to create a rule in a correlation scenario, refer to Creating Rules in a Correlation Scenario.
Click the APPLY CHANGES button at the top of the menu bar to activate your configuration changes.
Result
Threat Defender continuously adapts its baseline of normal behavior. The number of false-positives is reduced with this graylisting approach.