Time-based Baselining
Objective
Threat Defender can be set up to learn what behavior is normal during a fixed period of time, the learning phase. When this learning phase is over, Threat Defender enforces the learned behavior, allowing only the learned communication and rejecting everything else.
The learning phase is established using a schedule. During this phase, Threat Defender operates like a normal switch but gathers data about the devices in the network and their communication paths. Once this learning phase is completed, Threat Defender can use this behavior data to make filtering decisions to allow learned traffic patterns and reject unknown traffic.
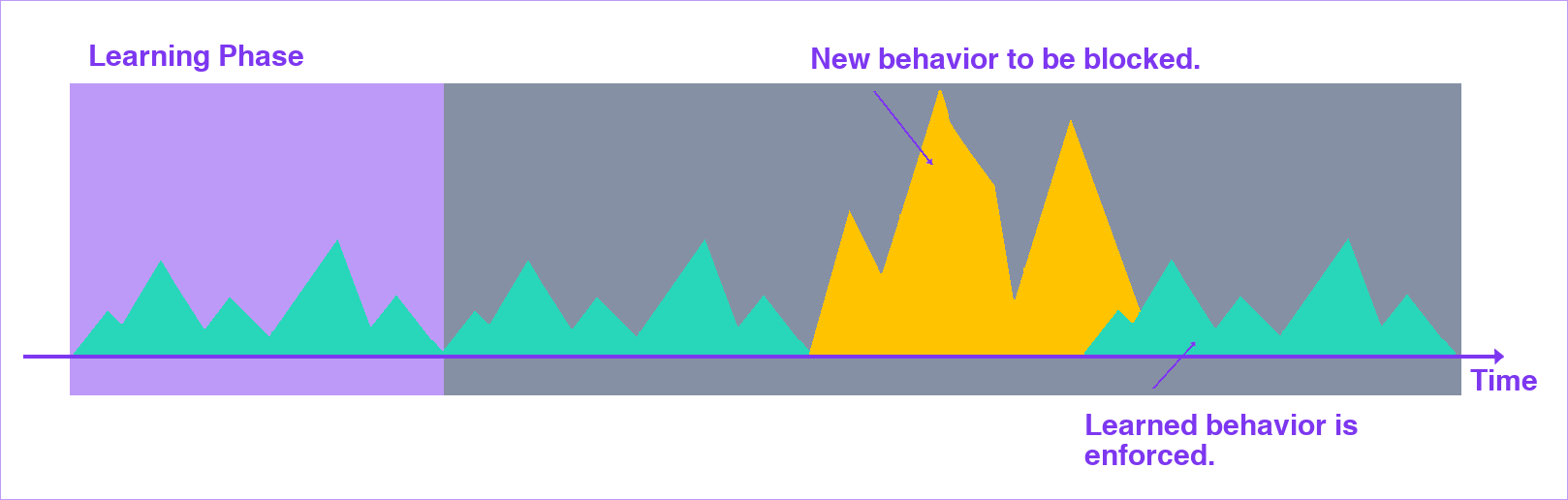
Time-based baselining.
Note
This scenario demonstrates the ability to allow dedicated connections (e.g. IP/IP, MAC address/MAC address, MAC address/port, etc.) between clients and servers. This can only be done using an event tracking table (ETT) because dynamic network objects do not store the client/server relationship.
Creating the “Learning Phase” Schedule
Set up a schedule that defines the learning phase.
Navigate to Policy > Schedules.
Click Add to add a new schedule.
Enter a Name, e.g.
Learning Phase.Optional: Enter a Note.
Enter the validity period using the date pickers under Valid from and Valid until.
Click Add Time Range to set a time during which the schedule is applied. You can add multiple time ranges.
Under Repeat, specify how often the learning phase is to be repeated automatically.
Click SAVE to store the schedule
Creating the Correlation Scenario
Navigate to Policy > Advanced Correlation. Create a new correlation scenario that provides the framework for the required event tracking table and rule set.
Creating the Event Tracking Table
In the correlation scenario, open the Event Tracking Tables tab. Create an event tracking table that stores the combinations of source (client) and destination (server) MAC address.
The following table shows the required settings of the event tracking tables:
Name |
Retention Time |
Primary |
Max. No. Primary |
Secondary |
Max. No. Secondary |
|---|---|---|---|---|---|
|
|
|
|
|
|
Note
Under Maximum Number of Primary Attributes, make sure that the table is large enough to fit your network.
Adapt the Retention Time for Event Tracking to the desired repetition intervals of the learning phase. Set it to
0if you want to store the entries indefinitely.
For detailed instructions on how to create an event tracking table, refer to Creating an Event Tracking Table.
Creating the Rule Set
In the correlation scenario, the following rules are needed for Threat Defender to learn traffic patterns and filter out any unknown traffic.
Rule 1 is only applied during the learning phase. It tracks the source and destination of the traffic in the event tracking table. Outside the learning phase, this rule is ignored.
Rule 2 is only applied outside the learning phase. If the source and destination of the detected traffic are contained in the event tracking table, the traffic is allowed. No further rules in this correlation scenario are processed for the respective traffic flows.
Rule 3 is only applied outside the learning phase. It blocks all remaining traffic, i.e. traffic that does not match the learned communication paths.
Rule |
Schedule |
Source |
Destination |
Condition |
Actions |
|---|---|---|---|---|---|
Include |
|
|
Add to Event Tracking Table |
||
Exclude |
|
|
Advanced Correlation Conditions: |
Final Action: |
|
Exclude |
|
|
Final Action: |
For detailed instructions on how to create a rule in a correlation scenario, refer to Creating Rules in a Correlation Scenario.
Click the APPLY CHANGES button at the top of the menu bar to activate your configuration changes.
Result
During the learning phase, Threat Defender learns which source and destination hosts are permitted to establish connections with each other. When the learning phase is completed, Threat Defender investigates all traffic and only allows the connections it identified during the learning phase.